Disable XML-RPC to prevent your site from attacks
I pretty sure that you all have seen the file name xmlrpc.php in the root folder of WordPress source pack. XML-RPC is a script that was set in active as default since WordPress version 3.5. It is a remote connection procedure of a Wodpress website that is using XML to transport data. And it now supports some CMS's API like WordPress API, Blogger API, Movable API, Pingback API, MetaWeblog API,…
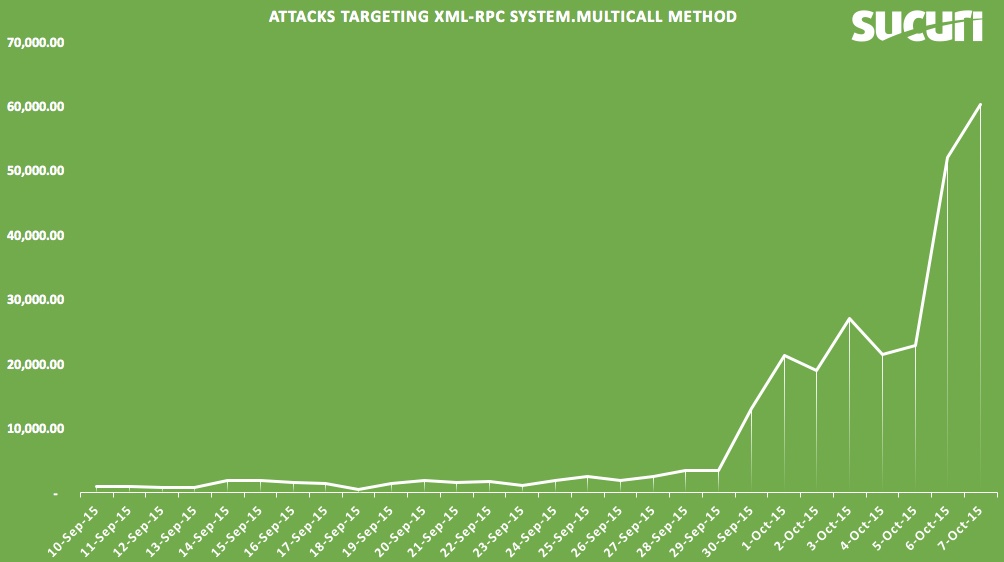
Normally, in WordPress, we use XML-RPC to post an article from another application like Window Live Writer, or any other service those connect with the website to post new article like IFTTT. But, since XML-RPC became too popular on WordPress, it brings out a new risk. Your website could be attacked with brute force attack method to scan password or hackers can even send a huge of request to your servers to flood your site - this method was also called HTTP Flood Attack, kind of DDoS attack.
XML-RPC based attacks is not a new method, but in recent months, lots of WordPress sites were attacked with through this file. So, if you have no to connect WordPress to outer services or applications, just disable XML-RPC to avoid attacks like this type.
How to know your website is under attack
The most simple way to know is your website under attack or not. That is, open the access_log file and search for unusual signs. You could be under attack through XML-RPC if you have a huge of access requests like below:
xxx.xxx.xxx.xxx - - [15/Sep/2016:12:54:49 +0700] "POST /xmlrpc.php HTTP/1.1" 200 0 "-" "Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.8.1.6) Gecko/20070725 Firefox/2.0.0.6"
xxx.xxx.xxx.xxx - - [15/Sep/2016:12:54:50 +0700] "POST /xmlrpc.php HTTP/1.1" 200 0 "-" "Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.8.1.6) Gecko/20070725 Firefox/2.0.0.6"
xxx.xxx.xxx.xxx - - [15/Sep/2016:12:54:50 +0700] "POST /xmlrpc.php HTTP/1.1" 200 0 "-" "Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.8.1.6) Gecko/20070725 Firefox/2.0.0.6"
xxx.xxx.xxx.xxx - - [15/Sep/2016:12:54:51 +0700] "POST /xmlrpc.php HTTP/1.1" 200 0 "-" "Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.8.1.6) Gecko/20070725 Firefox/2.0.0.6"
xxx.xxx.xxx.xxx - - [15/Sep/2016:12:54:51 +0700] "POST /xmlrpc.php HTTP/1.1" 200 0 "-" "Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.8.1.6) Gecko/20070725 Firefox/2.0.0.6"
xxx.xxx.xxx.xxx - - [15/Sep/2016:12:54:52 +0700] "POST /xmlrpc.php HTTP/1.1" 200 0 "-" "Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.8
How to restrict XML-RPC attacks
To restrict attacks with this method, the most simple way is restrict this file to execute. Please note that you should not remove/delete it because it is a part of WordPress source code, it could causes errors or trouble us when we update WordPress. Btw, we can try these options:
Restrict xmlrpc.php file on .htaccess
If you're using Shared Host or installed Apache server, just insert these lines of code in .htaccess file under root folder of the website:
<files xmlrpc.php>
order allow,deny
deny from all
</files>
Restrict xmlrpc.php on NGINX
If you're using NGINX as backend (use with PHP-FPM), just put these lines after the domain configuration file on NGINX:
location = /xmlrpc.php {
deny all;
access_log off;
log_not_found off;
}
Then restart NGINX:
service nginx restart
Restrict xmlrpc.php with iThemes Security plugin
If you're not able to use two above way, you can try a pre-built function of iThemes security - this will save you a lot of time. Like other WordPress security plugins, the plugin has included a function to disable XML_RPC and disable Pingback (you should do this if you feel it's necessary). You can also enable it at any time in Security -> Settings -> WordPress Tweak and select Disable XML-RPC.
If you're using NGINX, please remember to restart NGINX after select this option.



Comments are closed.